Why iOS security is better than Android?
Many business owners and leaders store important information on their phones. They use mobile devices for emails, banking, contracts, and communication. But cyber threats are growing. Hackers target smartphones to steal data or send harmful software.
Apple says it builds iPhones with strong security. But how safe is it really? Can iPhones protect business users from hackers, phishing, and malware? This blog explains Apple’s security system, compares it to Android, and helps you understand how to keep your business safe.
Table of Contents
- How Apple Protects Your Data
- iPhone vs. Android: Which is Safer?
- Common Cyber Threats for Business Users
- How to Protect Your Business with Apple’s Security Tools
- Final Thoughts: Is Apple the Best Choice for Security?

How Apple Protects Your Data
Security is important for business owners who store sensitive data on their phones. Hackers target mobile devices to steal information, install harmful software, and trick users into revealing passwords. A security breach can lead to financial losses, data leaks, and reputation damage. To prevent this, Apple has developed strong security features to keep iPhones safe from cyber threats.
Hardware-Based Encryption
Apple protects user data with hardware-based encryption. This means that every file, message, and password is stored in a way that makes it difficult for hackers to access. Unlike other devices, iPhones encrypt data directly on the chip, making it nearly impossible to extract information without the right credentials. Even if someone steals your phone, they cannot read the data without your passcode or biometric verification.
This encryption is always active, whether the phone is locked or turned off. When you enter your passcode, Face ID, or Touch ID, the system decrypts the necessary data instantly. This process happens without slowing down the phone’s performance, ensuring security without inconvenience.
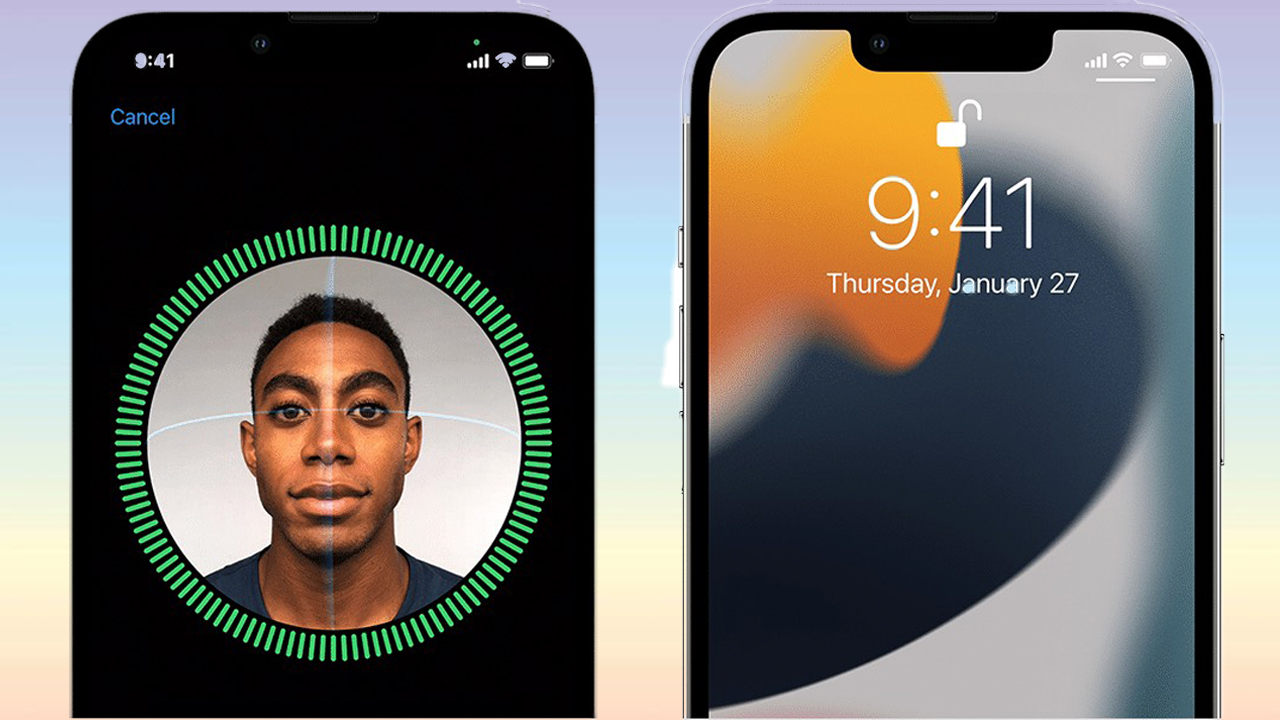
Face ID and Touch ID
For extra security, Apple uses biometric authentication through Face ID and Touch ID. Face ID scans over 30,000 points on your face to verify your identity, while Touch ID analyzes your fingerprint to unlock the device. These technologies are more secure than traditional passcodes, as they rely on unique biological data.
Even if someone tries to trick Face ID using a photo or mask, Apple's anti-spoofing technology can detect the difference. The system requires the user’s attention, ensuring that a phone cannot be unlocked when the owner is unconscious or not looking at the screen. For businesses, this prevents unauthorized access to important files, banking apps, and confidential messages.
End-to-End Encryption for Communication
Messages and calls contain important business information. To protect communication, Apple uses end-to-end encryption for iMessage and FaceTime. This means that only the sender and receiver can read the messages or hear the call. Even Apple cannot access this data, making it more secure than standard SMS and phone calls.
Other messaging platforms may store copies of conversations on their servers, increasing the risk of leaks. But with Apple’s encryption, data is never stored in a way that hackers or even Apple itself can access. This makes iPhones a preferred choice for business leaders, lawyers, and executives handling sensitive communication.
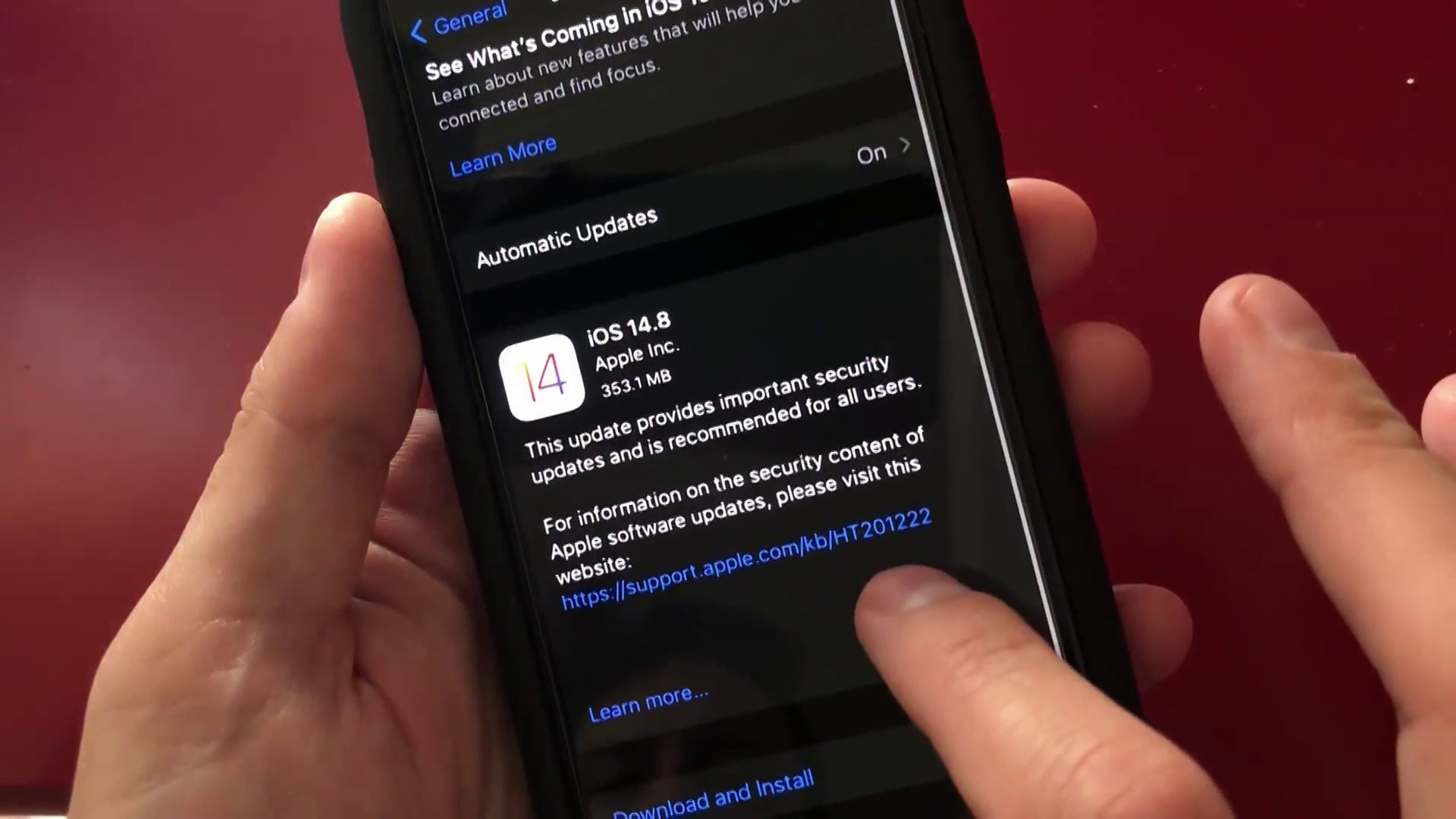
Frequent Security Updates
Hackers constantly find new ways to attack devices. Apple addresses this by releasing regular software updates that fix security issues and improve protection. These updates ensure that iPhones remain secure against the latest cyber threats.
Unlike many Android devices that delay updates or stop receiving security patches after a few years, Apple provides long-term support for iPhones. Businesses using iPhones benefit from timely security improvements, reducing the risk of data breaches.
Mobile Device Management (MDM) for Businesses
Apple offers Mobile Device Management (MDM) for companies that want to control and protect their employees' devices. MDM allows businesses to enforce security policies, limit access to certain apps, and remotely erase data if a device is lost or stolen. This helps organizations manage security across multiple devices efficiently.
Companies that deal with sensitive client data, such as finance and healthcare firms, use MDM to protect confidential information. By setting up strict security rules, businesses can prevent unauthorized access and reduce the risk of internal leaks.

iPhone vs. Android – Which is Safer?
Business owners often ask whether iPhones or Android devices offer better security. Both platforms have security features, but they work in different ways. Apple follows a closed system approach, while Android is more open and customizable. These differences affect how well each platform can protect business data.
| Security Feature | iPhone | Android |
|---|---|---|
| App Security | Strict App Store review, minimal malware | More malware due to third-party app sources |
| Software Updates | Fast, consistent updates for 5-6 years | Updates depend on manufacturer, often delayed |
| Phishing Protection | Safari warnings, Mail Privacy Protection | Varies by brand, inconsistent security |
| Device Encryption | Default strong encryption, cannot be turned off | Some models allow encryption to be disabled |
App Security & Malware Protection
One of the biggest security risks on mobile devices comes from malicious apps. Apple has a strict App Store review process that reduces the chance of malware-infected apps reaching users. Each app is checked before it is allowed on the App Store. If an app is found to have security risks, Apple removes it immediately.
In contrast, Android allows users to download apps from multiple sources, including third-party stores. This increases the risk of malware infections. Many Android users unknowingly install harmful apps that steal data or track activities. According to cybersecurity reports, Android devices are responsible for over 97% of mobile malware cases.
Software Updates & Long-Term Security
Apple provides long-term security updates for iPhones, ensuring that even older devices remain protected. When Apple releases a security patch, all compatible iPhones receive it at the same time. This means that most iPhone users are running the latest security updates.
Android, on the other hand, has fragmented software updates. Security updates depend on phone manufacturers and carriers, leading to delays. Some Android brands stop providing updates after just two to three years, leaving devices vulnerable to cyber threats. In comparison, iPhones receive security support for at least five to six years.
Protection Against Phishing Attacks
Phishing attacks are a major security threat to businesses. Hackers send fake emails or messages to trick users into revealing personal information. Apple has built anti-phishing tools into iOS to protect users from such scams.
For example, Safari has Fraudulent Website Warning, which alerts users if they visit a risky website. Mail Privacy Protection hides user IP addresses, preventing senders from tracking email activity. Android also has security features, but they vary by manufacturer and may not be as consistent across devices.
Device Encryption & Data Protection
Both iPhones and Android devices offer device encryption, but Apple has stronger default encryption settings. iPhones encrypt all data automatically and require user authentication for access. Even law enforcement agencies cannot bypass iPhone encryption without user permission.
Android devices also offer encryption, but some lower-end models have weaker security implementations. Additionally, Android users can disable encryption, leaving their data exposed. iPhones do not allow users to turn off encryption, ensuring consistent security across all devices.
If security is a top priority, iPhones are generally the safer choice. However, users should still follow best practices, such as enabling two-factor authentication and being cautious with links and emails.
Common Cyber Threats for Business Users
Business professionals store sensitive information on their phones, including financial data, client details, and private documents. Cybercriminals often target smartphones because they hold valuable data. Understanding the most common threats can help businesses take the right steps to stay protected.
Phishing Attacks
Phishing is one of the biggest threats to business users. Hackers send fake emails or text messages that look real, tricking users into sharing passwords or financial details. Some phishing attempts include links to fake login pages that steal credentials.
Apple devices include security features like Mail Privacy Protection and Safari’s Intelligent Tracking Prevention to block phishing attempts. However, the best protection is user awareness. Never click on suspicious links or enter personal details on unverified websites.
Malware and Spyware
Malware is software that hackers use to steal data or control a device. Spyware is a type of malware that secretly tracks user activity, collecting passwords, emails, and banking details. Many businesses have lost money due to malware infections.
While Android users face a higher risk of malware, iPhones are not completely immune. Apple’s App Store review process helps prevent harmful apps from being installed. Still, business users should avoid downloading apps from unknown sources and regularly update their devices.
Public Wi-Fi Risks
Many business users work remotely and connect to public Wi-Fi in airports, hotels, or cafes. However, public networks are not secure and can allow hackers to intercept data. This puts sensitive business emails, banking details, and login credentials at risk.
Apple’s VPN settings and automatic encryption for data transfers help reduce risks. Business users should also use a VPN service when connecting to public Wi-Fi and avoid accessing financial accounts on open networks.
Device Theft and Unauthorized Access
Losing a smartphone can expose sensitive company information. If a stolen phone is not protected, hackers can access emails, business apps, and stored passwords. This can lead to financial fraud or data breaches.
Apple provides Find My iPhone, which allows users to lock and erase a lost device remotely. Face ID, Touch ID, and strong passcodes also prevent unauthorized access, making it difficult for thieves to unlock an iPhone.
SIM Swapping Attacks
A SIM swap attack happens when a hacker tricks a phone carrier into transferring a user’s phone number to a new SIM card. This allows the hacker to bypass two-factor authentication (2FA) and gain access to business accounts.
To prevent SIM swapping, users should set up a PIN for their mobile carrier account and use physical security keys instead of SMS-based two-factor authentication. Apple also offers security recommendations in iOS settings to help users improve their protection.
Business Email Compromise (BEC)
Hackers target businesses by impersonating executives or employees to request money transfers or sensitive documents. These scams often come from emails that look real but have slight changes in spelling or domain names.
Apple’s Mail app warns users when receiving emails from unknown senders. However, businesses should also train employees to verify all financial requests before making payments and avoid sharing company details over email.
How to Protect Your Business with Apple’s Security Tools
Apple provides built-in security features that help business users protect their data. While iPhones have strong security by default, users must take extra steps to maximize protection. Below are the best practices to keep sensitive business information safe.
Enable Two-Factor Authentication (2FA)
Two-factor authentication (2FA) adds an extra layer of security to Apple IDs and business accounts. Instead of just using a password, 2FA requires an additional code sent to a trusted device. This makes it harder for hackers to access accounts, even if they steal a password.
Business users should enable 2FA for all important accounts, including email, banking, and company tools. Apple also supports security keys, which provide physical authentication for even stronger protection.
Use Apple’s Privacy Features
Apple includes privacy-focused tools that help users control who can access their data. Business professionals should take advantage of these features:
- Mail Privacy Protection – Hides your IP address from email senders.
- App Tracking Transparency – Prevents apps from collecting unnecessary data.
- Lockdown Mode – Adds extreme security for users who face high cyber threats.
Regularly Update iOS and Apps
Keeping your iPhone updated is one of the easiest ways to improve security. Apple releases regular security patches to fix vulnerabilities and protect against new cyber threats. Businesses should make sure all employees install iOS updates as soon as they become available.
Similarly, updating business apps ensures that they receive the latest security improvements. Older versions of apps may contain security flaws that hackers can exploit.
Secure Business Devices with MDM
For companies managing multiple employees and devices, Mobile Device Management (MDM) is an essential tool. MDM allows businesses to:
- Remotely wipe lost or stolen devices to prevent data leaks.
- Control which apps and services employees can access.
- Enforce strong security policies across all company devices.
Many large companies and government agencies rely on Apple’s MDM solutions to protect sensitive data. Business owners should consider setting up MDM to improve security, compliance, and device management.
Be Cautious with Public Wi-Fi
Public Wi-Fi networks are often unsecured and easy to hack. Cybercriminals can intercept data from unprotected connections, putting emails, banking details, and company files at risk.
To stay safe, business users should avoid using public Wi-Fi for sensitive transactions. If necessary, they should use a VPN (Virtual Private Network) to encrypt their internet connection and protect their data.
Final Thoughts: Is Apple the Best Choice for Security?
Apple’s security features provide strong protection for business users. Regular updates, encryption, and privacy tools make iPhones one of the safest choices for professionals handling sensitive data.
However, technology alone cannot prevent all cyber threats. Business users must follow best security practices, such as enabling two-factor authentication, using strong passwords, and staying alert against phishing scams.
By using these security tools and best practices, business users can protect their iPhones and prevent cyberattacks. Taking a proactive approach to security ensures that sensitive company data remains safe in today’s digital world.
Key Takeaways
- Enable Two-Factor Authentication (2FA) to add extra security to business accounts.
- Use Apple’s privacy features to block unauthorized tracking and protect personal data.
- Update iOS and apps regularly to stay protected against the latest security threats.
- Secure business devices with Mobile Device Management (MDM) for better control.
- Avoid public Wi-Fi risks by using a VPN for safer browsing.